Hackers create the possibility of new things entering the world. Not always great things, or even good things, but new things.
What Was GhostSec?
On Wednesday, January 7, 2015, two masked brothers carrying assault rifles burst into the offices of the Parisian satirical newspaper Charlie Hebdo and killed 12 people. Many others were injured. The brothers, who were members of al-Qaeda, fled the offices, fleeing across Paris for the next several days. During that time a policewomen was shot and killed in what seemed to be an unrelated incident in another part of the city. However, there was a connection: an associate of the brothers conducting the attacks was responsible for killing the police officer and taking hostages at a kosher supermarket. The associate had pledged his allegiance to the Islamic State of Iraq in the Levant (ISIL). Eventually police killed all three of the attackers (BBC 2015).
There were numerous public demonstrations and denouncements against the attacks across the globe. “Je suis Charlie” became a unifying slogan, expressing global civil society’s solidarity against terrorist organizations. Online, Anonymous created a campaign, “Operation Charlie Hebdo” or #OpCharlieHebdo, to take down terrorist organizations related to the attack:
We will track you everywhere on the planet, nowhere will you be safe. We are Anonymous. We are legion. We do not forget. We do not forgive. Be afraid of us, Islamic State and Al Qaeda—you will get our vengeance (International Business Times 2015).
Anonymous members declared war on politically violent Islamic extremists. Some Anons said it was their democratic duty to engage in the international political battle against groups. “[We will] track down all jihadist activities online and bring down Twitter and Facebook accounts of jihadists as well as close down any of their YouTube channels,” they said (International Business Times 2015).

The Anonymous declaration spawned multiple efforts to eradicate the online presence of terrorists. GhostSec was one such group that began targeting the Islamic State (ISIS) shortly after the call to cyber arms.[1] GhostSec’s main focus was ISIS, but it also went after other organizations such as Boko Haram, Al Shabaab, and Hamas. GhostSec members were both “horrified by ISIS’s atrocities” and concerned by the inability of governments to counter ISIS online:
The FBI has repeatedly admitted that. So, we got involved in #OpISIS in order to significantly slow ISIS down—recruitment and propaganda. We also wanted to be able to thwart attacks by collecting intel and turning that over to law enforcement (personal communication with GhostSec member Ransacker; March 2016).
In January 2015, GhostSec became an online citizen’s response to international political violence, working independently of the state but also willing to contribute to its goals. The core members of GhostSec were AnonCyberGost, WauchulaGhost, DigitaShadow, Comedianon, TorReaper, ISHunter, and GhostSecPI. The focus was to take down “daesh” in all its online manifestations.
GhostSec included women and men in its ranks, many ex-members of the U.S. military, and information technology (IT) and media professionals. There was a loose division of labor, with some members working the intelligence-gathering angle while other ghosts concentrated on the technical side of ISIS “hunting.” One ghost handled media requests and published a GhostSec Update website (https://medium.com/@GhostSec). The GhostSec project was coordinated through encrypted messaging applications, encrypted email, and, more publicly, on Twitter.
At first GhostSec was a “classic” instance of an Anonymous formation: they were indeed anonymous, and their information about ISIS was available to all. The ghosts were a mystery, but the point was to make ISIS as transparent as possible so that the extremist group’s online presence could be frustrated and erased. And the efforts of GhostSec were valuable to everyone including the U.S. government. In the beginning, GhostSec never worked directly with the U.S. government, but some of its core members built a bridge to U.S. officials.
A few GhostSec members communicated with terrorist analyst Michael Smith II of the defense consulting firm Kronos Advisory. Smith, a prominent consultant to Congress about ISIS, became a liaison between GhostSec activities and the government (Segall 2015). This relationship with Smith became emblematic of differences within GhostSec. Some members wanted to retain their autonomy and anonymity, while three members—DigitaShadow, ISHunter and GhostSecPI—opted to work more directly for the American state cause. The three left GhostSec in November 2015, shed their Anonymous affiliation, and founded the Ghost Security Group (GSG) (https://ghostsecuritygroup.com/). The remaining GhostSec members remained Anonymous. The split, says GhostSec, was not about sharing or not sharing information with U.S. authorities; rather, it was more about having a formal arrangement with the federal government. There was also disagreement about getting paid to hunt down ISIS. Those who remained felt that going after ISIS was more of a cause than a job. “We do this for free,” said one GhostSec hunter. Or, as TorReaper put it: “The intel…became a commodity that had to be protected and so stopped getting shared with the group’s followers” (Raincoaster 2015). After the split, GhostSec continued on, remaining within the Anonymous fold. Meanwhile, the market consumed GSG via the state.
GhostSec’s initial focus was on websites. The first step was to report the website to the host. If nothing was done, then GhostSec moved on and attacked “…first by attempting to breach the site, then by ddos [distributed denial of service] as a last resort. Breach attacks will include sql injection, XSS attacks and brute force attacks” (Raincoaster 2015). Eventually ISIS’s flow of social media activity became so huge in 2016 that GhostSec shifted away from bringing down websites and moved toward looking for direct “…threats, propaganda, etc. Any actionable intel…” that could then be sent to U.S. law enforcement agencies (Rajan 2016). To do this, GhostSec focused almost exclusively on Twitter accounts. The hacking group claimed to have removed more than 50,000 Twitter accounts by 2015 (Stone 2015). GhostSec worked with any individuals or groups who wanted to contribute by calling out suspected Twitter accounts and/or websites.[2] The process involved a swarm of participants whose findings were processed by GhostSec members. Suspicious accounts were then reported to Twitter through its website (https://support.twitter.com/forms/abusiveuser.)
For GhostSec, the fight against Twitter remained online. The battle was waged in cyberspace, but there were also offline results : a decrease in ISIS’s ability to spread its propaganda and garner more recruits. It wasn’t entirely one-sided. ISIS sympathizers did retaliate against GhostSec members, mainly via verbal cyber rantings. Nevertheless, GhostSec was not significantly counter-hacked.
In late summer of 2016, GhostSec’s success caused another shift in the group, pulling them into a merger with BlackOps Cyber, a private group affiliated with the international corporation BlackOps Partners (http://www.blackopscyber.com/home.html). With the merger, GhostSec dropped its Anonymous mask/affiliation to become part of a CyberHUMINT counter-terrorism team. The transformation meant deeper connections to international policing: Interpol, MI5, and others. Hardt and Negri (2004) might say the move solidified them as a part of Empire, “enlisted in the global armies at the service of capital, subjugated in the global strategies of servile inclusion and violent marginalization” (2014:159).
Meanwhile, WauchulaGhost kept his Anonymous stance to fight alone as #GhostofNoNation. GhostSec was done, but hacking free of feds and capitalism continued. In the spirit of a Multitude stance (Hardt and Negri 2004), WauchulaGhost proclaimed to me, he fights for others: “Everything I do is for the People…this is a free service.” Some of WauchulaGhost’s accomplishments included defacing ISIS followers’ Twitter accounts and websites with lulz images of goats and pro-LGBTQ imagery. [3]
State, Empire, or Multitude Minions?
GhostSec was a group of hacktivists, originally aligned with Anonymous, attacking politically violent Islamic groups, including Al-Shabaab, Boko Haram, and the Islamic State (IS). GhostSec wanted to expose extremist Twitter accounts and take down their online presence. And it did. The goal was to prevent the “bad guys” from using cybertools to support their violence in Somalia, Nigeria, Libya, and Syria. As such, GhostSec was a humanitarian cause that prevented the territorialization of cyberspace by terrorists. It was a noble cause, a cyber battle, almost mythic. Was it so simple, though: good versus bad? And what was the desired outcome?
On one level, it would appear that GhostSec was doing its part to curb potential violence. GhostSec was severing an extremist group’s networking tool, effectively “neutering…[their] ability to use Twitter to broadcast its message outside of its core audience…reducing the organization’s ability to manipulate public opinion and attract new recruits (Berger and Morgan 2015:56).
But did these actions address the deeper problem of why Al-Shabaab and others exist? These Islamic fighter groups were against the Western post-Westphalia liberal state. So was it possible that GhostSec’s actions were merely reproducing the same state structures (Althusser 2014) that ISIS and others so adamantly opposed? Or had GhostSec found a new way, a political action that shed state thinking (Bourdieu 2014)? It could be that GhostSec was effectively de-territorializing communication that had been territorialized for violence. If so, GhostSec was a piracy movement, carving out openings or temporary autonomous zones (Bey 1987) in the name of human rights. Or perhaps GhostSec was merely a privateer, “a private warrior” that generated profit from the global war on terror (de Zeeuw 2015:3).
The story above is about the role of GhostSec in international politics, specifically examining whether the hacktivist group was state-aiding, Empire-building, or Multitude-fulfilling (Hardt and Negri 2000). GhostSec was borne from the larger, amorphous movement known as Anonymous that had already executed a wide range of actions on the internet, from Operation Avenge Assange to Project Chanology to #OpTunisia to Operation AntiSec. As anthropologist Gabriella Coleman (2014) details in Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous, Anonymous has used multiple tactics as well as multiple ideological stances. While the overriding premise of the movement seems to be “Anonymous is not unanimous” and information should flow freely (Coleman 2014:106), it has “no consistent philosophy or political program” (Coleman 2014:3). Nevertheless, it is vulnerable to grander sociopolitical forces, such as states, that attempt to capture the movement for its/their own needs.
With GhostSec we see a new, complex manifestation of Anonymous. It’s a triadic struggle between the exogenous forces of the State, Empire, and the Multitude (Hardt and Negri 2000, 2004). The weapons of GhostSec are XSS and DDOS attacks, webpage defacements, and straight-out lulz-screwing with Islamic extremist Twitter accounts. The complexity began when the Anonymous group split in fall 2015 (Auerbach 2015). The apparent success of GhostSec in its efforts to deter ISIS and others prompted the United States government to ask the Anonymous cell for intel help, which tore the group open via competing sociopolitical forces: the State, Empire, and the Multitude. It was the Weberian, hierarchical, bureaucratic apparatus versus “the decentered and deterritorializing apparatus of rule that progressively incorporates the entire global realm” (Hardt and Negri 2000:xii) versus the autonomous force that “has the capacity to create society on its own” (Hardt and Negri 2004:225). The tug of war resulted in the creation of the splinter faction, the GSG. The now nonprofit organization was then pulled into the fold of the State. As for the original GhostSec, it morphed into a transcendental arm of Empire, a force that considers violence and war legitimate when “in the service of right and peace” (Hardt and Negri 2000:15).
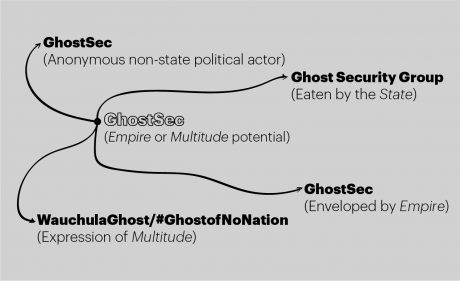
But the morphing of GhostSec did not end there (See Figure 3). This version had its own internal schisms. It broke asunder, and core member WauchulaGhost became a solo Anonymous warrior. The rest of GhostSec merged with BlackOps Cyber, which was part of a private, international intel agency. In the end, it seemed that only WauchulaGhost moved into the realm of the Multitude, a nomad, “plural and multiple,” a new democratic form a la Hardt and Negri (2004:99).
The fact that GhostSec took advantage of the erosion of state-based authority appears to be part of something different, possibly new, in international politics. GhostSec may be an expression of the Empire force as envisioned by Hardt and Negri (2000). GhostSec did not align with one single state, but rather contributed to the global formation of a distributed and nonstate-centric sovereign sociopolitical force. In effect, GhostSec would become a part of the production of Empire’s war factory, or could be a part of the Multitude dynamic that could transform “through historical action and create a new world,” a new democratic order (Hardt and Negri 2000:159). So even though the trickster lulz Anonymous may jump out and raspberry the world while it “takes down” a terrorist group’s web presence, it still must consider who benefits from its antics. Are they feeding the State? Boosting Empire? Or could they be entering the Multitude: “the only social subject capable of realizing democracy, that is, the rule of everyone by everyone” (Hardt and Negri 2004:100)?